Adding Microsoft Single Sign-On (SSO) is no different from any other integration in WISdom from the perspective of the integrations page interaction, but getting the required values from Entra is more involved than most of the others. This article provides a walkthrough of the Entra side of this configuration process.
Overview
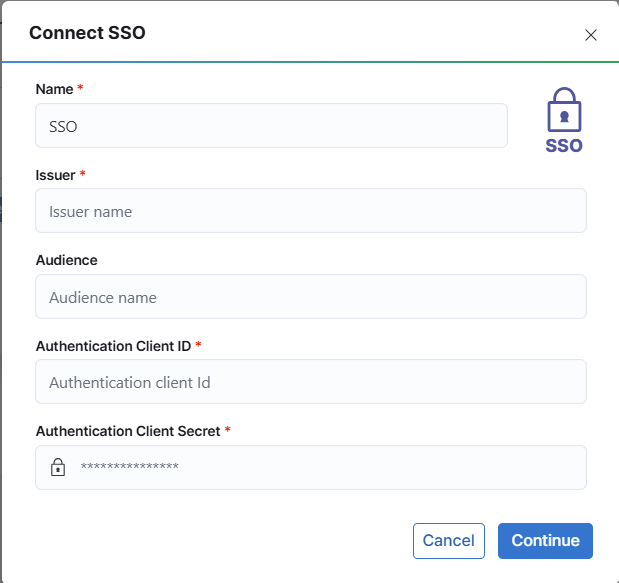
In order to use your own identity provider with WISdom you need to configure integration both in WISdom and in your identity provider. This document will guide you to do the following:
- Create an OIDC compliant “Application” in your Azure Entra account that is specific for supporting WISdom SSO.
- Create WISdom SSO credentials for that Application.
- Configure that Application to trust WISdom.
- Retrieve various configuration related values from that new Application to share with the WISdom SSO solution.
Note that WISdom SSO currently supports Client Credentials only. PKCE is not supported for verification.
Create a new Entra Application to use your Entra Identities for SSO
- Log into Azure and go to Entra.
- On left navigation menu choose Manage --> App Registrations.
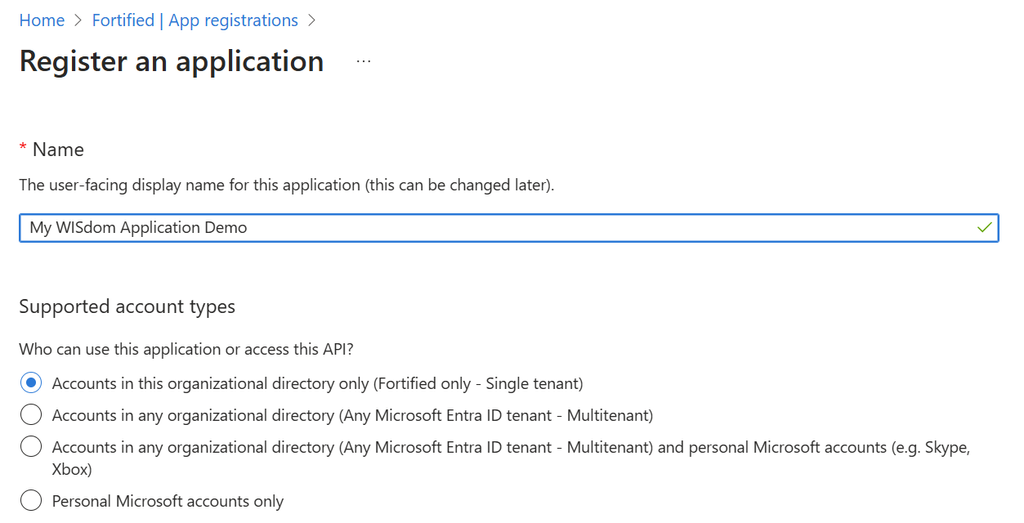
- Choose “New Registration.”
- Enter the name you want to use.
Create Application Client Credentials to allow WISdom integration with your Application
-
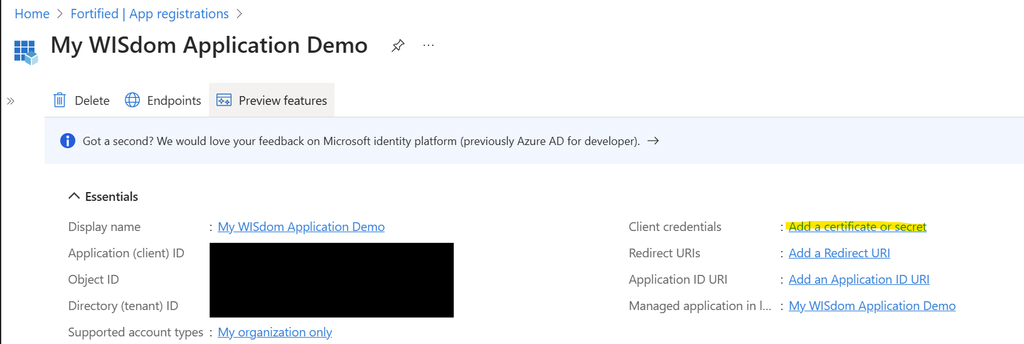
On the main Application page you choose “Add a certificate or secret”
-
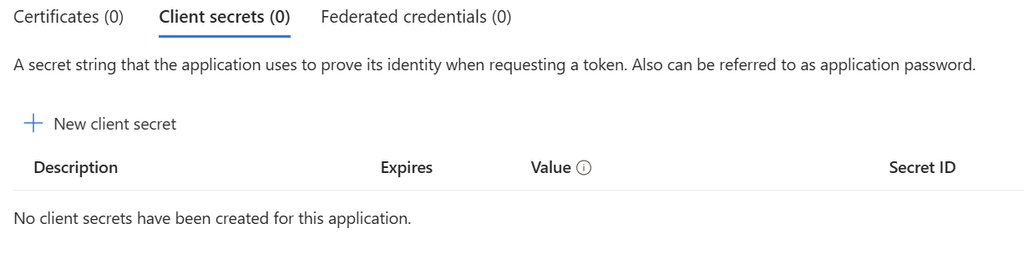
Choose "+New client secret."
-
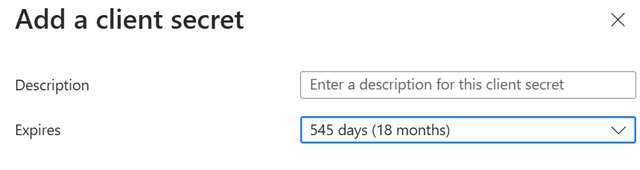
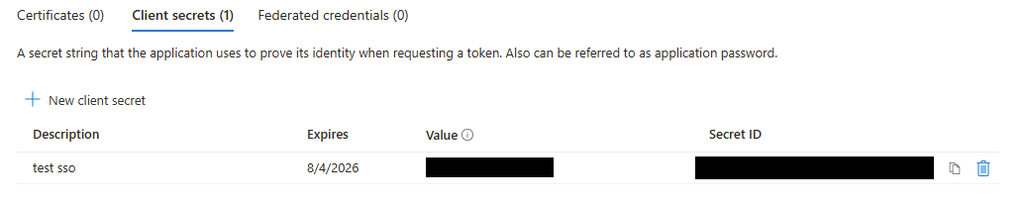
Enter the name of the secret and the expiration.
- Note that you can choose an Expires value that conforms to your organization's standards, but please be sure to note when it will expire. It will need to be refreshed in WISdom prior to expiration to avoid disruptions in access.
- Save your secret “Value” before continuing. This is your Client Credential Secret and can only be done at time of creation. Save the “Secret ID” as well. This is your Client Credential ID.
- These are the credentials you will provide in your SSO configuration.
Update a Whitelist of Allowed WISdom Redirect URLs in your Application
- Return back to the new application and choose “Add an Application ID URI.”
- Choose “Add a Platform.”
- Choose "Web" platform.
- Under “Web / Redirect URIs“ add the following URIs:
- https://app.fortifiedwisdom.com/bff/v1/oauth/oidc-callback
- https://app.fortifiedwisdom.com/login
- Under “Front-channel logout URL” enter:
- https://app.fortifiedwisdom.com/logout
- Under “Implicit grant and hybrid flows” choose “ID tokens (used for implicit and hybrid flows)“ check box.
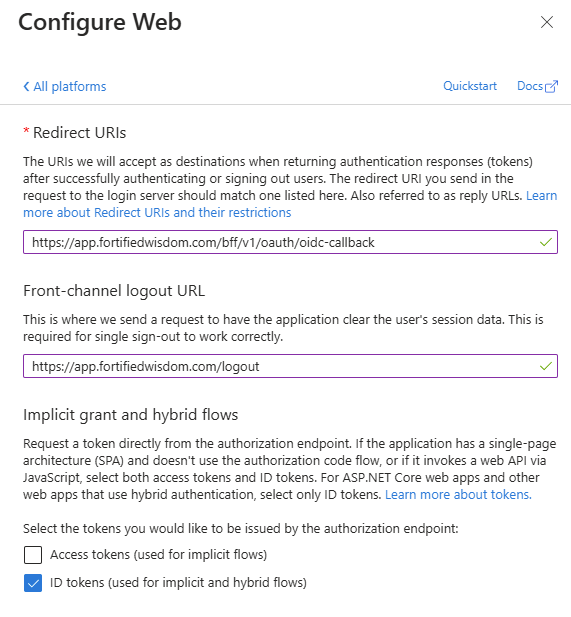
- Click Save.
Retrieve the New Application Values to configure SSO in WISdom
- Back at the application page you need to find the URLs to share are part of SSO configuration. Choose “Endpoints”.
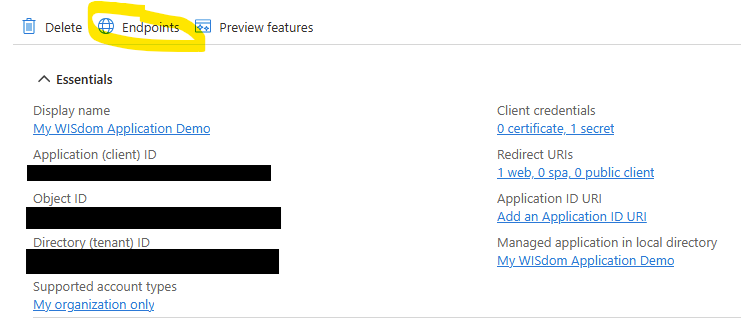
- Copy the “OpenID Connect metadata document” and open the endpoint in a new browser tab.
- Copy values for
- “jwks_uri" to get the Public Key URL.
- “token_endpoint" to get the Token URL.
- “authorization_endpoint" to get the Authentication URL.
- “issuer" to get the Token Issuer.
- Enter these values for your SSO configuration with WISdom along with your Client Credentials.
- Audience field value is optional but would be populated from the aud field of the JWT.
- Audience field value is optional but would be populated from the aud field of the JWT.